Introduction
Are you tired of manual and time-consuming data processes that slow down your business operations? Streamlining your operations is crucial for staying competitive in today’s fast-paced business environment and EDI via AS2 protocol integration can come to your rescue.
Say goodbye to paper trails, manual data entry, and potential errors. Start sending your EDI files today using the AS2 protocol. This innovative technology allows for seamless electronic communication and data exchange between trading partners, making it an invaluable tool for streamlining your supply chain, reducing costs, and improving overall efficiency, from automating order processing to enhancing inventory management.
Key Takeaways
- EDI via AS2 (Applicability Statement 2) is a protocol for securely exchanging EDI documents over the Internet.
- AS2 ensures data privacy, integrity, and authentication, making it a popular choice for secure B2B transactions.
- It enables real-time data exchange, reducing delays compared to traditional EDI communication methods.
- AS2 compliance is widely required by major retailers, making it essential for businesses in various industries.
History of AS2

The AS2 protocol was developed in the late 1990s by the Internet Engineering Task Force (IETF), in response to the need for secure data exchange without relying on traditional methods.
In 2002, the protocol gained significant traction when Walmart, one of the world’s largest retailers, mandated AS2 for its suppliers. This requirement created a wave of AS2 adoption, which spread across various industries.
Over time, AS2 became an EDI standard endorsed by numerous organizations, setting the foundation for modern, internet-based data exchange methods.
What is AS2?
AS2, or Applicability Statement 2, is a protocol that allows secure and dependable data transfer over the Internet. The use of AS2 allows organizations to establish direct connections with their trading partners, creating a more streamlined communication channel.
Originally designed to enable secure EDI transactions, AS2 has gained popularity due to its encryption capabilities, which help protect sensitive data during transmission. The protocol uses secure HTTP (HTTPS) as the transport layer and supports digital certificates for encryption and digital signatures for data integrity.
This ensures that files sent via AS2 reach their intended recipient without tampering or unauthorized access. The enhanced security measures provided by AS2 also help businesses comply with industry regulations, thus avoiding potential fines and maintaining a trustworthy reputation.
AS2 protocol is designed with three core features security, integrity, and non-reputation
- Security: Sensitive data is protected in AS2 through the transport layer which wraps EDI data in a secure “envelope” and sends it over the internet.
- Integrity: The data is encrypted, and the identity of the sender and the integrity of the payload are ensured using pre-established digital certificates that are validated upon each connection.
- Non-Reputation: The receiver of the data returns a signed message containing a Message Disposition Notification (MDN) confirming the successful transfer.
A simple AS2 setup involves two computers – a client and a server – connecting in a point-to-point manner via the web. Sending EDI documents via AS2 requires the receiving organization’s server to be always ‘listening”. Like a call to a phone without an answering machine, the message will be missing if the AS2 server is not available. As a result of this high availability requirement, many businesses prefer to use an EDI provider to help them with EDI AS2 integration and provide ongoing maintenance and support.
Traditional methods of data exchange, such as email, fax, or FTP, can be susceptible to data loss or corruption. In contrast, AS2 ensures that every message is acknowledged and validated upon receipt, providing a clear audit trail. This level of reliability is crucial for maintaining accurate records and ensuring compliance with industry regulations. Companies can have confidence that their transactions are executed correctly, and that sensitive information remains protected.
What are the Key Attributes of the AS2 Protocol?
The AS2 protocol has several defining attributes that make it a popular choice for secure data exchange:
- Security: AS2 uses encryption and digital signatures to secure data, making it one of the safest methods for transferring sensitive information over the internet.
- Authentication: By verifying the sender’s identity using digital certificates, AS2 ensures that files come from trusted sources.
- Non-Repudiation: AS2 provides proof of delivery through Message Disposition Notifications (MDNs), which serve as receipts that confirm a successful transfer. This feature is essential for industries where compliance and accountability are crucial.
- Data Integrity: With AS2, files cannot be modified during transmission. The protocol employs cryptographic hashing to confirm that the data sent matches the data received.
- Real-Time Exchange: Unlike traditional VANs, AS2 facilitates direct, real-time data transfer, which enhances communication speed and operational efficiency.
- Cost-Effective: AS2 allows businesses to bypass intermediaries like VANs, reducing transaction costs and giving organizations greater control over data exchanges.
Who Uses EDI via AS2 Integration?

AS2 is widely used by companies that need to exchange sensitive data securely and efficiently. This includes sectors like:
- Retail: Large retail chains, like Walmart, require suppliers to use AS2 to ensure fast, secure, and reliable transactions.
- Manufacturing: Many manufacturing firms use AS2 to exchange supply chain information, such as order details, invoices, and shipping updates.
- Healthcare: Hospitals and healthcare providers rely on AS2 to transmit time sensitive information in compliance with regulations.
- Logistics and Transportation: AS2 is essential for logistics companies that handle various EDI documents, including shipping manifests, to ensure smooth operations.
- Government Agencies: Certain government agencies and contractors use AS2 to securely transmit official documents.
How do I Send and Receive EDI via AS2?
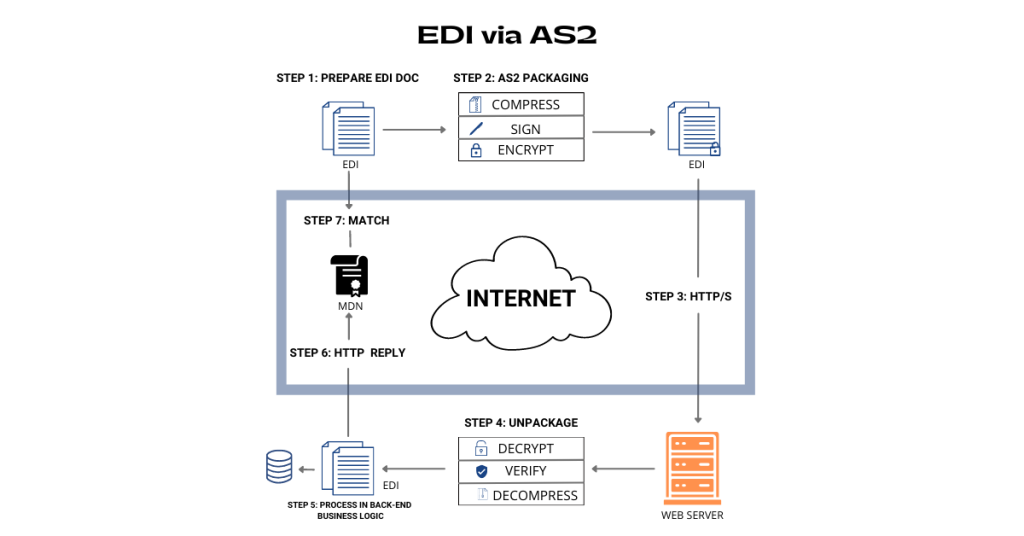
Step 1 – EDI Document Preparation
Documents are prepared in a standard EDI format to be sent over AS2
Step 2 – AS2 Packaging
The document is packaged to send via AS2 using three layers of transmission:
Compression – A document may be compressed using a compression algorithm to reduce the size of the data being transferred
Signature – Sender signs the document using the exchanged certificates and keys to ensure data integrity
Encryption – The data is typically encrypted using the receiver’s public encryption key, so only the proper recipient will be able to extract the document
Step 3 – Message Delivery
The data is transmitted securely over HTTP/S. A Message Disposition Notification (MDN) is returned to the sender confirming receipt.
Step 4 – AS2 Unpacking
Upon receiving the document at the receiver’s end, the document is decrypted using the receiver’s private key and then verified by using the sender’s public key and finally the document will be decompressed
Step 5 – EDI Processing
The document is then passed by the AS2 receiver system to any backend process that handles the data. The next systems and workflows perform any additional business logic and make the document available to business users.
Step 6 – Confirmation of Receipt
The receiving organization uses AS2 or EDI software to extract the message and send message confirmation receipts such as the MDN and EDI functional acknowledgment (997) to the sender.
Step 7 – Sender Validation (MDN processing)
The sender receives the MDN and validates the receipt signature and completes any other configured data integrity checks that confirm the successful delivery transaction.
AS1 vs AS2 vs AS3 vs AS4 – The Key Differences
Attribute | AS1 | AS2 | As3 | AS4 |
|---|---|---|---|---|
| Transport Protocol | SMTP (email based) | HTTP/HTTPs | FTP | Web services |
| Security | Limited | High (encryption signatures) | Moderate | Very high |
| Delivery Confirmation | No MDN | MDN | No MDN | Receipt acknowledgement |
| Real Time Capability | No | Yes | No | Yes |
| Use Case | Early EDI and small data transfers | Widely adopted in retail, healthcare and logistics | Lower cost VAN alternative | Complex, modern B2B environments |
Benefits of Using AS2 Protocol
- Enhanced Security: AS2 offers high security through encryption, digital signatures, and authentication, making it suitable for industries that handle sensitive data.
- Cost Savings: By eliminating the need for a VAN, AS2 reduces data transmission costs, especially for businesses with high transaction volumes.
- Real-Time Communication: AS2 enables real-time data exchange, improving operational efficiency and allowing quick responses to supply chain demands.
- Reliability and Accountability: With MDNs, companies have proof of successful delivery, helping ensure compliance and enhancing accountability.
- Scalability: AS2 can handle high transaction volumes, making it suitable for businesses of all sizes.
- Compliance with Standards: AS2 is compliant with various data security and privacy standards, making it ideal for regulated industries like healthcare and finance.
Disadvantages of Using AS2 Protocol
While AS2 offers a range of benefits, there are also some drawbacks that organizations should consider before implementing it:
- Complex Setup and Maintenance: Setting up AS2 requires specific technical knowledge and expertise, including configuring digital certificates, encryption settings, and security protocols. This complexity can make AS2 challenging for smaller companies with limited IT resources.
- Initial Cost of Implementation: Although AS2 can reduce long-term costs by bypassing VANs, the initial implementation cost can be high. Companies may need to invest in AS2-compliant software, servers, and digital certificates, along with training for their IT teams.
- Reliance on Internet Connectivity: AS2 relies on the Internet for data transmission, making it vulnerable to disruptions in connectivity. Any internet outages or slowdowns can impact the speed and reliability of data exchange.
- Digital Certificate Management: Managing digital certificates can be cumbersome, especially for businesses with multiple trading partners. Certificates expire periodically and need to be updated to maintain secure communication, which can create additional administrative overhead.
- Scalability Limitations: While AS2 is suitable for high transaction volumes, managing multiple trading partners and maintaining connections with each one can become complex as businesses grow, especially if different partners have varying security and compliance requirements.
- Limited Compatibility with New Protocols: AS2 is primarily designed for HTTP-based data transmission, which can limit compatibility with newer protocols or specific modern applications. Organizations looking for broader protocol flexibility may find AS2 limiting.
- No Built-in Archiving or Tracking: AS2 itself does not include built-in features for archiving or tracking transactions. Many organizations implement third-party solutions for these purposes, which can add to costs and operational complexity.
- Potential Compliance Burden: Due to AS2’s security requirements, companies must stay vigilant about compliance. For industries with stringent regulations (such as healthcare or finance), maintaining compliance can require continuous monitoring and updating of security protocols, which can be time-consuming.
Choosing the Right EDI Provider for Your Business
Selecting the right EDI provider is a critical decision that can significantly impact the success of your EDI implementation. Begin by evaluating the provider’s expertise and experience in your specific industry. Look for a vendor with a proven history of successful EDI implementations, particularly those utilizing AS2. Their familiarity with industry standards and practices will be invaluable in guiding you through the process.
Consider the range of features and services offered by potential EDI providers. A comprehensive solution should include support for AS2, integration capabilities with existing systems, and user-friendly interfaces. Additionally, assess the level of customer support available. Responsive support is crucial, especially during the initial implementation phase and ongoing operations. A provider that offers training, technical assistance, and resources can make a significant difference in your experience.
Finally, evaluate the scalability of the EDI solution. Your business needs may evolve, and it is essential to choose a provider that can accommodate growth. Whether you plan to expand your operations or increase transaction volumes, select a provider with flexible solutions that can adapt to your changing requirements. By carefully considering these factors, you can choose an EDI provider that aligns with your business goals and drives successful implementation.
Why Choose Commport Communications as Your EDI Provider
Commport stands out as an exceptional EDI provider for AS2 integration due to its robust expertise, reliable infrastructure, and client-centered approach to secure data transmission. Here’s why Commport should be your top choice for businesses seeking seamless EDI integration:
- Extensive Industry Experience: With over 35 years of experience in EDI and data integration, Commport understands the complexities of AS2 implementation across various industries. This knowledge allows Commport to streamline the setup process, reduce errors, and ensure high data integrity.
- Comprehensive AS2 Support and Maintenance: Setting up AS2 involves digital certificates, encryption, and custom configurations that can be daunting. Commport simplifies this process with full-service support, from initial configuration to ongoing maintenance, ensuring that your AS2 setup remains secure and compliant.
- Advanced Security and Compliance: Commport is a SOC II Type II compliant company, and we prioritize data security, employing advanced encryption methods, digital certificates, and robust compliance protocols. This commitment to security ensures that your EDI transactions are protected from unauthorized access, aligning with strict industry standards.
- Scalable Infrastructure for Growing Needs: Commport’s EDI solution is highly scalable, accommodating businesses of all sizes, from small companies to global enterprises. Our infrastructure is designed to handle high transaction volumes and multiple trading partner connections, making it adaptable as your business grows.
- Reliable Monitoring and Troubleshooting: Commport offers continuous monitoring and real-time troubleshooting, minimizing disruptions and ensuring that data flows smoothly between trading partners. Their initiative-taking support team can address issues quickly, maximizing uptime and operational efficiency.
- Tailored EDI Solutions: Unlike generic EDI providers, Commport offers customized solutions that address the specific needs of each client. We take the time to understand your business requirements, making adjustments to your AS2 integration that fit your unique workflows and trading partner demands.
- End-to-End Integration Expertise: Commport supports businesses through every step of the EDI integration process, from planning and implementation to onboarding new trading partners. Our team of EDI experts assists in aligning AS2 with your broader IT ecosystem, ensuring seamless integration with ERP, WMS, and other internal systems.
- Cost-Effective Solutions: Commport’s EDI solutions are designed to provide excellent value, reducing long-term costs associated with setting up your company’s own IT infrastructure and unnecessary manual processes. Our scalable solutions also help prevent additional expenses as your business expands, delivering long-term savings.
Conclusion
The AS2 protocol remains one of the most trusted and widely used methods for secure data exchange. Its robust security features, real-time capabilities, and cost savings make it a preferred choice for organizations across various industries. Whether for retail, healthcare, or logistics, AS2 continues to meet the demands of modern data exchange with reliability and scalability. For businesses considering adopting AS2, understanding the protocol’s fundamentals and its benefits is key to leveraging secure data exchange and improving supply chain efficiency.
Commport EDI Solutions
Need Help? Download: EDI Buyers Guide
Unlock the full potential of your supply chain with our comprehensive EDI Buyer's Guide — your first step towards seamless, efficient, and error-free transactions
Frequently Asked Questions
AS2 is primarily used for the secure and real-time transfer of data over the internet, often for EDI transactions between trading partners.
Yes, AS2 is scalable and can support high transaction volumes, making it suitable for large organization
AS2 uses Message Disposition Notifications (MDNs) as receipts, confirming successful data delivery between trading partners.
No, not all companies require AS2. It is ideal for those needing real-time, secure communication, especially in industries like retail, logistics, and healthcare.
Yes, AS2 provides strong security through encryption and digital signatures, making it suitable for transmitting sensitive data like financial or healthcare information.





